Dating App That Claims 50 Million Users Suffered a Data Breach

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password protected database that contained approximately 2.3 million records. Upon further investigation, it became clear that these records were associated with multiple dating applications contained in a single database.
A majority of the records referred to an application called 419 Dating - Chat & Flirt. However, inside the database, I also saw information related to other dating apps called Meet You - Local Dating App by Enjoy Social App, and Speed Dating App For American by MyCircle Network Corp. The presence of what appeared to be logos and development files pertaining to these apps in the same database may be suggestive of the likelihood that all three dating apps are owned or developed by the same company using different names. There were also documents related to a couple of location-tracking applications found in the database, though we can’t assure they are related in any way to 419 Dating due to the lack of information available online that the companies are connected. According to multiple listings of software download sites, 419 Dating - Chat & Flirt is developed by a Chinese company called SILING APP (also visible in the web archive). I immediately sent a responsible disclosure notice and although the database was quickly secured no one ever replied. The app used to be available on the Google Play Store but was removed shortly after my notification. However, the app is still available on many other websites. Per its own advertisement campaign, the 419 Dating app claims to have 50 million users worldwide.
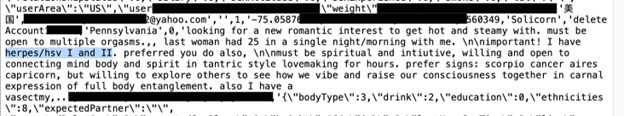
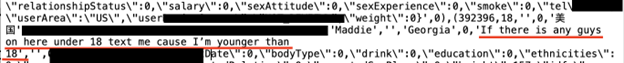
The database appears to contain a massive number of user records that include customer names, account numbers, emails, passwords, and more. In total, the database contained more than 600 compressed server logs. When I reviewed a single server log, I saw a massive amount of email addresses. Considering this was a limited sample, it is possible that the rest of the files contain many more emails. Should this information fall in the wrong hands, all these users could potentially be subjected to spam, phishing attacks, or other malware infections.
 This screenshot from the Google Play Store shows what the user interface of the app looked like when it was available there.
This screenshot from the Google Play Store shows what the user interface of the app looked like when it was available there.
What the database contained:
- Total number of records: 2,357,896 with a total size of 340.6 GB
- 959,571 images of users. Some of these images were NSFW (not safe for work) and contained sexually explicit images. I saw close up pictures of body parts and those with the users’ faces. These identifiable images combined with names and emails could be a potential risk to the user.
- A single backup log contained 236,681 Gmail addresses, 15,703 Yahoo Mail accounts, 3,872 iCloud addresses, as well as many other addresses from various email providers. Remember this was only a sampling of one server log out of 600 from the folder db_backup. In the same backup file, there were records of more than 500 profiles containing the word “escort” and offering sexual services; they had associated phone numbers, email addresses, and social media accounts.
- The database also contained exposed Software Development Kit (SDK) files, which are packages or collections of software tools, libraries, documentation, and resources that developers use to create software applications for a specific platform or framework. This could lead to the creation of applications with hidden malicious functionalities or vulnerabilities.
Server logs are a wealth of information.
Server logs often record a wide range of information about server activity, including web traffic, server errors, and user activity. Server logs may at times record unencrypted usernames, passwords, and personal data. In this case, the database appeared to contain detailed information about the users, including images and their profiles.
The risk of an application exposing an API or private key is significant and poses serious risks to the users. A private key is a secret cryptographic key that is used to authenticate and authorize access to an API service account. If cyber criminals gain access to an application’s private key, they could potentially gain unauthorized access to all of the resources that a specific account has access to, such as additional sensitive data or other permission-based actions.
Another potential vulnerability that is often overlooked is App Permissions. These permissions are a way for apps to access certain functions or data on your device. While these permissions are necessary for apps to function properly, they also pose a certain degree of risk to your privacy and security. It is important to review the permissions requested by each app before installing it. You should also regularly review the permissions of existing apps and revoke any that are not used or needed. I also recommend using a mobile security app to monitor and manage app permissions on your device. This is a general good practice and is not directly linked to the apps discussed in this article.
According to the documentation of the 419 Dating app on the Google Play Store, this app requests access to the device’s storage. This means that, when you install it on your phone, the app can potentially read, modify, or delete your photos, media, files, device ID, call information, and anything else that you have stored in your device. The user agrees to allow the app to receive data from the Internet, get full network access, prevent devices from sleeping, view network connections, and change audio settings.
The risks of a dating application data breach.
Like any data breach, that of a dating app can pose significant risks to the privacy and security of its users. Dating apps often require users to provide sensitive information, such as sexual preferences or health conditions. This type of information could be used to discriminate against individuals or be used for blackmail purposes. Furthermore, compromised personal information such as the user’s real names and email addresses could make these individuals a potential target for cyber criminals.
When using the app, the user has a layer of privacy, but the data breach could potentially expose their real name, email address, and geographic location. In this case, the profile accounts contained explicit information such as sexual experience, information concerning details of the user’s last sexual encounter, and other highly sensitive personal information. I saw multiple accounts where the user admitted to having a sexually transmitted disease or other health conditions.
The potential breach of so many email accounts could potentially put users at risk of targeted phishing attempts and scam attacks. When combined with detailed user data, cybercriminals can launch highly targeted fraudulent messages or phishing emails that may put the app users at risk of financial losses or identity theft. Any application developer that collects and stores the data of its users is generally expected to have an obligation to protect sensitive information. Another good practice is to educate users on safe online practices and provide them with resources to help them protect their personal information.
The potential exposure of user IDs and passwords would allow unauthorized access to user’s accounts. Once inside the user admin area, it would be possible for cyber criminals to see the message history and any payment details or other personal information associated with the account. Moreover, by reviewing the message history of the victim, cyber criminals can potentially access the personal information of people within the victim’s social circle. Thus, social engineering poses a unique risk to more than just the app’s users.
Another notable concern from the discovery were mentions of escort services as well as users seemingly offering sexual services both online and in person. There have been numerous reported cases of individuals using dating apps to lure and exploit vulnerable people for sex-trafficking purposes. We highlight the importance of being aware of potential risks and exercising caution when communicating with strangers online. However, we must stress that we are not implying that the 419 Dating App is knowingly used for this purpose, only that a potential risk could exist – particularly given the indication that the app’s terms and conditions may not be thoroughly enforced.
Although the app appears to be a legitimate dating service, it is interesting to note that the name of the application mirrors the classic "419" term, which is often used to describe scams that originate from Nigeria, named after the section of the Nigerian Criminal Code that deals with fraud. These scams typically involve someone requesting money or personal information in exchange for a promise of a larger reward or financial gain. We are not implying that 419 Dating - Chat & Flirt or any of the abovementioned apps are connected in any way to fraud or crimes, nor are we saying that users are at imminent risk.
It is unclear how long the database was exposed or if anyone else may have gained access to these images, records, and server logs. We publish our findings for educational purposes and to highlight the real world risks of data exposures. Users who have used these or other dating apps and believe they may have had their personal data exposed should be vigilant of suspicious activity.